rfid security access control system abstract Abstract. Aims: The study was conducted to develop a basic security system that integrates Radio Frequency Identification (RFID), an electromagnetic lock, and a GSM Module . Where can I find a NFC reader? (Canada) Request. Hi! I completely missed the 3DS when I .
0 · rfid microcontroller
1 · rfid based access control pdf
2 · rfid access control system
3 · electromagnetic access control system pdf
Overall, the Samsung Gear S2 is a versatile smartwatch that offers a range of features to enhance the user's daily activities. With its modern design, high .
Abstract. Aims: The study was conducted to develop a basic security system that integrates Radio Frequency Identification (RFID), an electromagnetic lock, and a GSM Module .Abstract. Aims: The study was conducted to develop a basic security system that integrates .
© 2008-2024 ResearchGate GmbH. All rights reserved. Terms; Privacy; IP Policy; Imprint
yarongtech rfid tag
Abstract: Access control is an important feature needed for the security of emerging smart and connected applications such as smart homes. This paper investigates cost effective . Abstract. Aims: The study was conducted to develop a basic security system that integrates Radio Frequency Identification (RFID), an electromagnetic lock, and a GSM Module to produce a lowcost.Abstract: Access control is an important feature needed for the security of emerging smart and connected applications such as smart homes. This paper investigates cost effective construction of a personalized access control system from off the shelf components.Also, we propose a mobile ap-plication that allows gate registration and serves as a door unlock key. The suggested access control model reduces in-stallation costs required, while maintaining good security. The system is fully wireless and uses .
Abstract. The subject of this bachelor thesis is security in access control systems using RFID. The amount of RFID systems is increasing and RFID is being used in more and more areas. Further, more ciphers and security systems are broken which makes it easier for individuals to obtain the materials and the knowledge needed to attack RFID systems.
rfid microcontroller
Abstract. The 3-factor authentication control system is aim at providing maximum security in com-pany’s stores, special utilities and premises where valuables are stored.This paper presents the design and implementation of an RFID access control for the IoT, with a security scheme based on Open-source hardware and the ATECC608A cryptographic processor to provide data integrity and confidentiality.

Abstract: This paper presents a design scheme that combines embedded technology with biometric technology to implement a RFID access control system based on Raspberry PI. This system adopted the open-source OpenCV and Dlib to develop the face feature extraction and authentication module. In this work we introduce an alternative access control scheme, which improves access control security while lowering the cost. In the proposed model, passive RFID tags are mounted near a turnstile or a smart door.
Abstract. RFID technology (pronounced “Arr-Eff-Eye-Dee” or “Arr-Fid”) is used for a wide variety of applications including access control, package identification, warehouse stock control, point-of-sale scanning, retail antitheft systems, toll-road passes, surgical instrument inventory, and even for identifying individual sheets of paper .
The study introduces a novel design and simulation of a role-based access control system that has been augmented with a facial recognition system, utilising the ESP32-CAM. Abstract. Aims: The study was conducted to develop a basic security system that integrates Radio Frequency Identification (RFID), an electromagnetic lock, and a GSM Module to produce a lowcost.
Abstract: Access control is an important feature needed for the security of emerging smart and connected applications such as smart homes. This paper investigates cost effective construction of a personalized access control system from off the shelf components.
Also, we propose a mobile ap-plication that allows gate registration and serves as a door unlock key. The suggested access control model reduces in-stallation costs required, while maintaining good security. The system is fully wireless and uses .Abstract. The subject of this bachelor thesis is security in access control systems using RFID. The amount of RFID systems is increasing and RFID is being used in more and more areas. Further, more ciphers and security systems are broken which makes it easier for individuals to obtain the materials and the knowledge needed to attack RFID systems.Abstract. The 3-factor authentication control system is aim at providing maximum security in com-pany’s stores, special utilities and premises where valuables are stored.
This paper presents the design and implementation of an RFID access control for the IoT, with a security scheme based on Open-source hardware and the ATECC608A cryptographic processor to provide data integrity and confidentiality.Abstract: This paper presents a design scheme that combines embedded technology with biometric technology to implement a RFID access control system based on Raspberry PI. This system adopted the open-source OpenCV and Dlib to develop the face feature extraction and authentication module.
women's rfid card wallet
In this work we introduce an alternative access control scheme, which improves access control security while lowering the cost. In the proposed model, passive RFID tags are mounted near a turnstile or a smart door.Abstract. RFID technology (pronounced “Arr-Eff-Eye-Dee” or “Arr-Fid”) is used for a wide variety of applications including access control, package identification, warehouse stock control, point-of-sale scanning, retail antitheft systems, toll-road passes, surgical instrument inventory, and even for identifying individual sheets of paper .
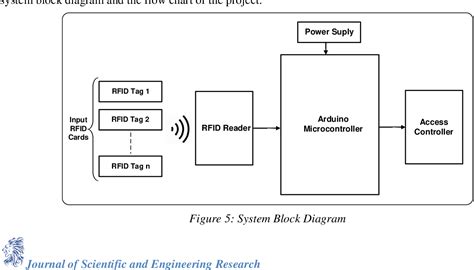
rfid based access control pdf
rfid access control system

women's credit card holder rfid
electromagnetic access control system pdf
Late to the party but i use two programs and 1 nfc card. Tagmo to write the amiibo using their database. And then an app called "Tag Writer" from NXP to erase the data on the card to .
rfid security access control system abstract|rfid access control system