7 types of security attacks on rfid systems A man-in-the-middle attack happens during the transmission of a signal. Like eavesdropping, the hacker listens for communicationbetween . See more RUSH. R. Penny 4 ATTs, 29 YDs. E. Elliott 26 ATTs, 137 YDs, 1 TD. REC. T. Lockett 4 RECs, 120 YDs. A. Cooper 7 RECs, 106 YDs. Recap. Box Score. Fast, updating NFL football game .
0 · what is rfid technology
1 · what is rfid security
2 · security attacks on rfid
3 · rfid systems
4 · rfid signal encryption
5 · rfid security vulnerabilities
6 · rfid security risks
7 · rfid security problems
Site-wide Card Declined Issues for Many People. I am having people I know personally contacting me saying their card was declined for my new Kickstarter campaign. They tried many cards .
what is rfid technology
Like most products, RFID tags and readers can be reverse engineered; however, it would take a lot of knowledge about the protocolsand features to be successful. Hackers would take apart the chip in order to find out how it works in order to receive the data from the IC. Purpose:Steal Information and/or Gain . See moreThis attack requires nothing more than the brain of a hacker and a cell phone. According to leading experts 1, power analysis attacks can be mounted on RFID systems by monitoring the power consumptionlevels of RFID tags. Researchers . See moreA man-in-the-middle attack happens during the transmission of a signal. Like eavesdropping, the hacker listens for communicationbetween . See more
A Denial of Service attack is the broad concept of an RFID system failure that is associated with an attack. These attacks are usually physical attacks like jamming the system with noise interference, blocking radio signals, or even removing or disabling RFID . See moreEavesdropping, like it sounds, occurs when an unauthorized RFID reader listens to conversations between a tag and reader then obtains important data. It is still necessary for the . See more
how to insert a sim card in a smart watch
some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized .Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and .
There are two types of disclosure attacks possible on the RFID system, such as .Generic Attacks. Sniffing of the communication between transponder and reader. .These security threats include attacks such as replay, disclosure, tracking, ofline guessing, .
RFID systems are susceptible to a broad range of malicious attacks ranging from .Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle and .In this work, we present a survey of recent works dealing with security and privacy in RFID . In this section, we discuss the several types of attacks that attackers can use to .
Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; however, it would take a lot of knowledge about the protocols and features to be successful.
some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2. There are two types of disclosure attacks possible on the RFID system, such as identity disclosure attack and full disclosure attack. In an identity disclosure attack, the attacker steals the identity of the tag.Generic Attacks. Sniffing of the communication between transponder and reader. Counterfeiting of the communication. Obtain UID, user data and meta data. Basic attack on structures and tags. Replay attack to fool the access control systems.
These security threats include attacks such as replay, disclosure, tracking, ofline guessing, denial of service attacks, and many more. In the last few decades, the researchers have suggested various security approaches to overcome these vulnerabilities. RFID systems are susceptible to a broad range of malicious attacks ranging from passive eavesdropping to active interference. For example, since simple RFID tags can be read without authorization, the contents of a handbag or a shopping cart can become visible to intruders without leaving a trace.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle and denial of service, RFID technology is, in particular, susceptible to spoof and power attacks. This section illustrates the different kinds of attacks on RFID systems.
In this work, we present a survey of recent works dealing with security and privacy in RFID systems. Particularly, we compare and classify them according to which part of RFID system each solution could be applied, taking into account different requirements and parameters including their conformity to RFID standards. In this section, we discuss the several types of attacks that attackers can use to exploit vulnerable RFID cards. These attacks can only be performed on chips for systems where only the UID is used to provide access or if the encryption .
what is rfid security
security attacks on rfid
Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; however, it would take a lot of knowledge about the protocols and features to be successful.
some of the most common types of attack on RFID tags: unauthorized disabling, unauthorized cloning, unauthorized tracking, and response replay. We introduce security mechanisms appropriate to defeat these attacks, and show how a recently proposed RFID authentication protocol uses them to achieve security.Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle, and denial of service, RFID technology is, in particular, susceptible to spoofing and power attacks (Figure 2). This section illustrates different kinds of attacks and provides countermeasures against these attacks. Fig. 2. There are two types of disclosure attacks possible on the RFID system, such as identity disclosure attack and full disclosure attack. In an identity disclosure attack, the attacker steals the identity of the tag.Generic Attacks. Sniffing of the communication between transponder and reader. Counterfeiting of the communication. Obtain UID, user data and meta data. Basic attack on structures and tags. Replay attack to fool the access control systems.
These security threats include attacks such as replay, disclosure, tracking, ofline guessing, denial of service attacks, and many more. In the last few decades, the researchers have suggested various security approaches to overcome these vulnerabilities. RFID systems are susceptible to a broad range of malicious attacks ranging from passive eavesdropping to active interference. For example, since simple RFID tags can be read without authorization, the contents of a handbag or a shopping cart can become visible to intruders without leaving a trace.
Besides being vulnerable to common attacks such as eavesdropping, man-in-the-middle and denial of service, RFID technology is, in particular, susceptible to spoof and power attacks. This section illustrates the different kinds of attacks on RFID systems.In this work, we present a survey of recent works dealing with security and privacy in RFID systems. Particularly, we compare and classify them according to which part of RFID system each solution could be applied, taking into account different requirements and parameters including their conformity to RFID standards.
lettore per smart card firma digitale
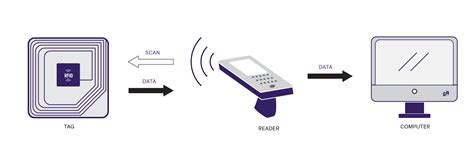
These challenges encourage exploration of alternate forms of device security for .Shows Java Card applet installed on a contact-less Smart Card and tag info. This app shows Secure Element applications (a.k.a Java Card applet or Smart Card application) .
7 types of security attacks on rfid systems|rfid security vulnerabilities