access control card administration Access control management is implementing tools, processes, and policies to ensure that each entity can and does access only the appropriate data and systems. What are the three types of access control? Three of the most common types of access control are: Rule-based . I got an NFC Reader with USB I want to get working on a M1 Macbook pro. The .
0 · wireless access control card readers
1 · types of access control cards
2 · card access control systems companies
3 · best key card access systems
4 · access control proximity cards
5 · access control card printers
6 · access control card calculator
7 · access card issuance daily monitoring
The app works with: – All NTAG215 NFC tags. – Flashiibo. – PowerTags. – N2 Elite Tags. so you can quickly restore your backups easely. You can also import your own .bin files if you prefer to keep your amiibo sealed. The app works .Posted on Nov 1, 2021 12:10 PM. On your iPhone, open the Shortcuts app. Tap on the Automation tab at the bottom of your screen. Tap on Create Personal Automation. Scroll down and select NFC. Tap on Scan. Put your iPhone near the NFC tag. Enter a name for your tag. .
Access control management is implementing tools, processes, and policies to ensure that each entity can and does access only the appropriate data and systems. What are the three types of access control? Three of the most common types of access control are: Rule-based . A badge access control system is a security solution that manages who can enter your building or specific areas within it. It uses electronic badges or keycards to ensure that only authorized individuals—like employees or .How can you use proximity reader access control technology to safeguard your facility? In this .
Everything you need to know about RBAC in one place. This article provides a .
Card access control systems have transformed security management across various sectors, . Access control management is implementing tools, processes, and policies to ensure that each entity can and does access only the appropriate data and systems. What are the three types of access control? Three of the most common types of access control are: Rule-based access control (RuBAC) Role-based access control (RBAC) A badge access control system is a security solution that manages who can enter your building or specific areas within it. It uses electronic badges or keycards to ensure that only authorized individuals—like employees or approved visitors—can enter secure spaces. When someone scans their badge at a reader, the system verifies their access.
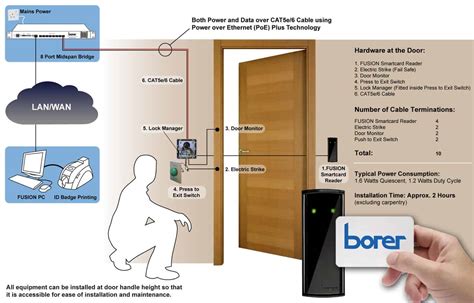
The EPS Managed Access administrators are able to manage cards, records, and many other programming needs. They can add new employees, and remove former ones, set specific activation dates or deactivate access cards, and even limit access to .How can you use proximity reader access control technology to safeguard your facility? In this article, we will discuss what proximity readers are, how an proximity access control system works, different types of door key card reader configurations and other considerations you must know before you install these devices in your facility. Everything you need to know about RBAC in one place. This article provides a comprehensive overview of role-based access control (RBAC) along with a guided approach to implementing, maintaining, and extending RBAC to suit the needs of your organization.Card access control systems have transformed security management across various sectors, offering unparalleled control and protection. These systems utilize advanced technology to regulate access based on the credentials embedded within access cards.
Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
wireless access control card readers

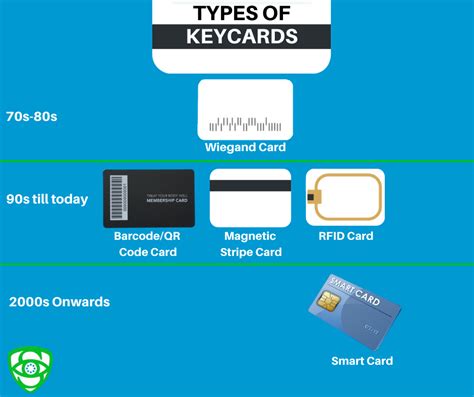
Access cards are the backbone of most card access control systems, providing a secure and convenient way to manage entry into buildings and secure areas. These cards, often the size of a credit card, hold essential data to grant or deny access.Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what circumstances. In the same way that keys and preapproved guest lists protect physical spaces, access control policies protect digital spaces.
rfid key card makers
Badge and ID card access control systems ensure that only authorized individuals can enter secured facilities, provide audit trails for regulatory compliance and incident investigations, and support administrators by allowing them to easily add, modify, or remove privileges associated with users. Access control management is implementing tools, processes, and policies to ensure that each entity can and does access only the appropriate data and systems. What are the three types of access control? Three of the most common types of access control are: Rule-based access control (RuBAC) Role-based access control (RBAC) A badge access control system is a security solution that manages who can enter your building or specific areas within it. It uses electronic badges or keycards to ensure that only authorized individuals—like employees or approved visitors—can enter secure spaces. When someone scans their badge at a reader, the system verifies their access.
The EPS Managed Access administrators are able to manage cards, records, and many other programming needs. They can add new employees, and remove former ones, set specific activation dates or deactivate access cards, and even limit access to .How can you use proximity reader access control technology to safeguard your facility? In this article, we will discuss what proximity readers are, how an proximity access control system works, different types of door key card reader configurations and other considerations you must know before you install these devices in your facility. Everything you need to know about RBAC in one place. This article provides a comprehensive overview of role-based access control (RBAC) along with a guided approach to implementing, maintaining, and extending RBAC to suit the needs of your organization.
types of access control cards
Card access control systems have transformed security management across various sectors, offering unparalleled control and protection. These systems utilize advanced technology to regulate access based on the credentials embedded within access cards. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access.
Access cards are the backbone of most card access control systems, providing a secure and convenient way to manage entry into buildings and secure areas. These cards, often the size of a credit card, hold essential data to grant or deny access.Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what circumstances. In the same way that keys and preapproved guest lists protect physical spaces, access control policies protect digital spaces.
card access control systems companies

rfid guard card
rfid inlay design
Berikut beberapa fungsi NFC pada HP : 1. Berbagi Foto dan Video. NFC dapat berfungsi untuk mengirim foto dan video secara nirkabel. Caranya simpel, Anda tinggal menempelkan bagian belakang HP ke logo .
access control card administration|access control card calculator