smart card based password authentication Password authentication with smart card is one of the most convenient and effective two- factor authentication mechanisms for remote systems to assure one communicating party of the legitimacy of the corresponding party by acquisition of corroborative evidence. Depending on the type of card used in your school, copying is not a simple task: .Cloning isn't necessary as the algorithm used for nfc with the emv cards is .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
When you write and store data on an NFC tag or card, any NFC reader enabled device can read from the tag and do actions based on that. If you are using an iPhone 6 or later, you can read and write NFC tags quickly. If you .Following are the features of NFC type-1 Tag: • Standard: ISO-14443A • Memory Size: 96 bytes • Speed: 106 Kbps • Data Access: Read/Write or Read Only • Collision mechanism: Data collision protection not available. • Compliant Products: Innovision Topaz • Pricing:Low See more
Password authentication with smart card is one of the most convenient and effective two- factor authentication mechanisms for remote systems to assure one communicating party of the .
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Password authentication with smart card is one of the most convenient and effective two- factor authentication mechanisms for remote systems to assure one communicating party of the legitimacy of the corresponding party by acquisition of corroborative evidence.
Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity. As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, and hundreds of this type of schemes have wave upon wave been proposed.
Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software. We also present a new efficient strong smart card based password authentication protocol that satisfies not only the minimum conditions but also advanced requirements like efficiency and mutual authentication. Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication: Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
In this paper, we will propose an improved and efficient smart-card-based password authentication and key agreement scheme. According to our analysis, the proposed scheme not only maintains the original secret requirement but also achieves mutual authentication and withstands the stolen-smart-card attack.
Like many other smart card-based authentication methods, the three schemes involve a set of users and a single server. Users access the resources by mutual authentication with server. The authentication usually includes four basic phases: registration, login, authentication, and password change.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Password authentication with smart card is one of the most convenient and effective two- factor authentication mechanisms for remote systems to assure one communicating party of the legitimacy of the corresponding party by acquisition of corroborative evidence.
Thales' smart cards offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as corporate ID badges, magnetic stripes and proximity.
As the most prevailing two-factor authentication mechanism, smart-card-based password authentication has been a subject of intensive research in the past two decades, and hundreds of this type of schemes have wave upon wave been proposed.Smart Card Authentication is a means of verifying users into enterprise resources using a physical card in tandem with a smart card reader and software. We also present a new efficient strong smart card based password authentication protocol that satisfies not only the minimum conditions but also advanced requirements like efficiency and mutual authentication. Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications. In this paper, we will propose an improved and efficient smart-card-based password authentication and key agreement scheme. According to our analysis, the proposed scheme not only maintains the original secret requirement but also achieves mutual authentication and withstands the stolen-smart-card attack.
rfid vault 12 credit card 2 passport sleeves
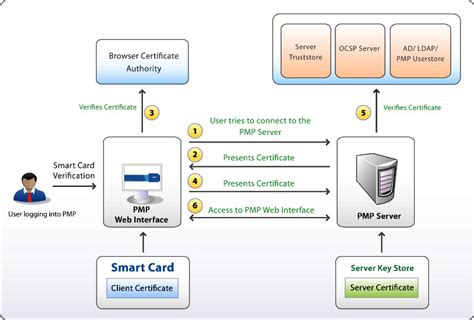
what is smart card authentication

Metrodroid for Android requires Android 4.1 or later, with NFC support. Some devices do not support MIFARE Classic. MIFARE Classic is not an NFC-compliant card format, so they can only be read on devices with NXP chipsets. .
smart card based password authentication|smart card authentication process