virtual smart card authentication requirements Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. FOOTBALL RADIO COVERAGE. Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games .
0 · Use Virtual Smart Cards
1 · Understanding and Evaluating Virtual S
2 · Implementing strong user authenticatio
3 · Get Started with Virtual Smart Cards
Fans can listen to free, live streaming audio of Auburn Sports Network radio .
Use Virtual Smart Cards
Customers using virtual smart cards are encouraged to move to Windows Hello .
Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for . Prerequisites. Step 1: Create the certificate template. Step 2: Create the TPM virtual smart card. Show 2 more. Warning. Windows Hello for Business and FIDO2 security keys are modern, two-factor authentication methods for Windows. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2.
dallas cowboys standings 2023
Understanding and Evaluating Virtual S
This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for .
Smart cards are physical authentication devices, which improve on the concept of a password by requiring that users actually have their smart card device with them to access the system, in addition to knowing the PIN, which provides access to the smart card. Virtual smart cards (VSCs) emulate the functionality of traditional smart cards, but . This feature offers a streamlined user sign-in experience—it replaces passwords with strong two-factor authentication by combining an enrolled device with a PIN or biometric user input for sign in. Windows Hello was easy to implement within our existing identity infrastructure and is compatible for use within our remote access solution. This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login. We recommend that a qualified domain administrator be in charge of the process and that you use these instructions as a guideline for deployment. This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed.
You can find system requirements, restrictions, and limitations when using Microsoft VSCs in the Microsoft TechNet article Use Virtual Smart Cards. You can connect a maximum of ten smart cards (including both physical smart cards and VSCs) simultaneously to a PC.
Prerequisites. Verify that the client device, remote desktops, RDS hosts, Connection Server host, and other Horizon components meet the smart card authentication requirements. See Smart Card Authentication Requirements. Verify that the device has a passcode. A passcode is required to create a virtual smart card. Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for .
Prerequisites. Step 1: Create the certificate template. Step 2: Create the TPM virtual smart card. Show 2 more. Warning. Windows Hello for Business and FIDO2 security keys are modern, two-factor authentication methods for Windows. Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2.This document presents an overview of TPM virtual smart cards as an option for strong authentication. It provides a means for evaluating virtual smart card use in an enterprise deployment, in addition to providing information necessary for . Smart cards are physical authentication devices, which improve on the concept of a password by requiring that users actually have their smart card device with them to access the system, in addition to knowing the PIN, which provides access to the smart card. Virtual smart cards (VSCs) emulate the functionality of traditional smart cards, but .
wild card games today scores
This feature offers a streamlined user sign-in experience—it replaces passwords with strong two-factor authentication by combining an enrolled device with a PIN or biometric user input for sign in. Windows Hello was easy to implement within our existing identity infrastructure and is compatible for use within our remote access solution.
This document covers the basic steps required to set up an Active Directory domain environment for smart card authentication, including considerations before provisioning YubiKeys for smart card login. We recommend that a qualified domain administrator be in charge of the process and that you use these instructions as a guideline for deployment.
This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed.
You can find system requirements, restrictions, and limitations when using Microsoft VSCs in the Microsoft TechNet article Use Virtual Smart Cards. You can connect a maximum of ten smart cards (including both physical smart cards and VSCs) simultaneously to a PC.
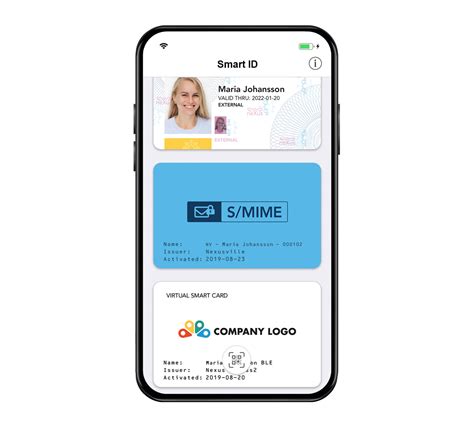
Implementing strong user authenticatio

August 31, 2023 4:00 pm CT. Nothing beats a Saturday listening to Auburn Sports Network’s all-day coverage of Auburn Tigers football in the fall. This season’s lineup within the Auburn Sports Network changes slightly, as Andy .
virtual smart card authentication requirements|Implementing strong user authenticatio