extensible authentication protocol method smart card EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. There are currently about 40 different methods defined. Methods defined in IETF RFCs include EAP-MD5, EAP-POTP, EAP-GTC, EAP-TLS, EAP-IKEv2, EAP-SIM, EAP-AKA, and EAP-AKA'. Additionally, a number of vendor-specific methods and new proposals exist. Commonly used modern metho. IC/ID RFID Reader Writer: NFC Reader Writer Scanner for 125khz/13.56Mhz Cards, Support Cracking IC Encrypted Cards, Driver-Free, LED Light Prompt,and USB Full Speed Interface with Software. $3999. Save 20% with coupon. FREE delivery Sun, Nov 10.
0 · radius authentication protocol
1 · network authentication protocol
2 · extensible authentication protocol windows 11
3 · extensible authentication protocol eap
4 · extensible authentication protocol
5 · eap method for authentication
6 · eap fast authentication protocol
7 · eap authentication protocol examples
A fraudulent NFC reader can still read your passive card data. You cannot disable .
It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption. EAP methods protect a specific portal so that . The Extensible Authentication Protocol (EAP) supports a variety of authentication methods, each designed to meet specific security requirements and operational contexts. Among the most significant are EAP-TLS, EAP .
Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily .EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. There are currently about 40 different methods defined. Methods defined in IETF RFCs include EAP-MD5, EAP-POTP, EAP-GTC, EAP-TLS, EAP-IKEv2, EAP-SIM, EAP-AKA, and EAP-AKA'. Additionally, a number of vendor-specific methods and new proposals exist. Commonly used modern metho.The Extensible Authentication Protocol (EAP Protocol) is a wireless network that builds on the authentication method used by the Point-to-Point Protocol (PPP). This protocol is commonly used to connect a computer to the Internet.
EAP ideally works on encrypted networks to transmit identifying information required for network authentication. Experts consider it a framework because it offers a range of authentication mechanisms for OTPs, token .Extensible Authentication Protocol (EAP) is an authentication framework commonly used in wireless networks and other security architectures. It allows the use of different authentication methods and provides a standardized way .These methods include token cards, Kerberos, One-Time Passwords (OTP), smart cards, Public Key Infrastructure (PKI), and more. The strength of EAP lies in its flexibility. It can support new .
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS .It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption. EAP methods protect a specific portal so that . The Extensible Authentication Protocol (EAP) supports a variety of authentication methods, each designed to meet specific security requirements and operational contexts. .
Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily .
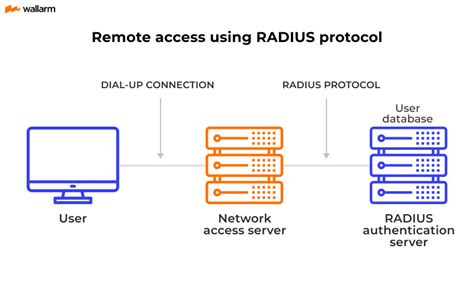
radius authentication protocol
The Lightweight Extensible Authentication Protocol (LEAP) method was developed by Cisco Systems prior to the IEEE ratification of the 802.11i security standard. [3] Cisco distributed the .The Extensible Authentication Protocol (EAP Protocol) is a wireless network that builds on the authentication method used by the Point-to-Point Protocol (PPP). This protocol is commonly . EAP ideally works on encrypted networks to transmit identifying information required for network authentication. Experts consider it a framework because it offers a range .Extensible Authentication Protocol (EAP) is an authentication framework commonly used in wireless networks and other security architectures. It allows the use of different authentication .
These methods include token cards, Kerberos, One-Time Passwords (OTP), smart cards, Public Key Infrastructure (PKI), and more. The strength of EAP lies in its flexibility. It can support new .This flexibility enables EAP to support different authentication mechanisms, such as passwords, digital certificates, smart cards, token-based authentication, biometrics, and more. The EAP .
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS .
It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption. EAP methods protect a specific portal so that . The Extensible Authentication Protocol (EAP) supports a variety of authentication methods, each designed to meet specific security requirements and operational contexts. .Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily .The Lightweight Extensible Authentication Protocol (LEAP) method was developed by Cisco Systems prior to the IEEE ratification of the 802.11i security standard. [3] Cisco distributed the .
The Extensible Authentication Protocol (EAP Protocol) is a wireless network that builds on the authentication method used by the Point-to-Point Protocol (PPP). This protocol is commonly . EAP ideally works on encrypted networks to transmit identifying information required for network authentication. Experts consider it a framework because it offers a range .Extensible Authentication Protocol (EAP) is an authentication framework commonly used in wireless networks and other security architectures. It allows the use of different authentication .These methods include token cards, Kerberos, One-Time Passwords (OTP), smart cards, Public Key Infrastructure (PKI), and more. The strength of EAP lies in its flexibility. It can support new .
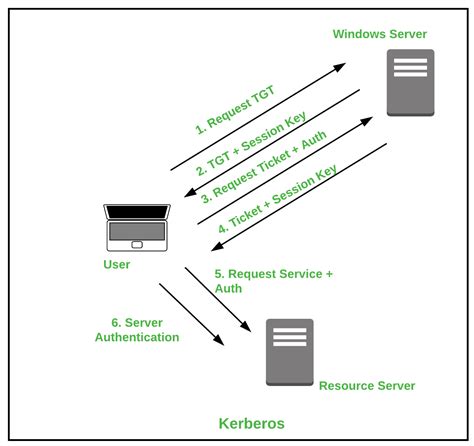
network authentication protocol
So it is possible that a bad write to the Capability Container has increased the .
extensible authentication protocol method smart card|eap fast authentication protocol